ChipMaster at Play
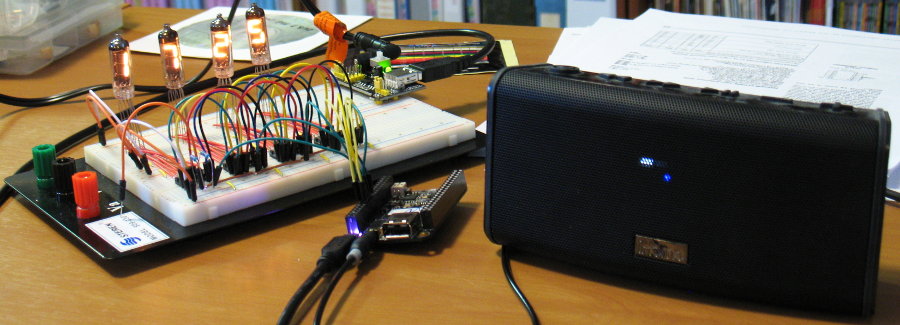
A C.H.I.P. wired up to tell time (visually & audibly) plus play some music!
This just in: I'm making a Poor Man's IDS for my personal cyber-defense! See below.
Welcome web travelers. When I was very young, in the 1970s, my dad woke me up, in the middle of the night, took me to his office and showed me how he could type a BASIC program to count to ten into a terminal connected to a mainframe computer. I was entranced! A machine that did anything you told it to do! WOW! Sometime later a TRS-80 model I level 2 came home. I have been passionate about computers, especially writing software, ever since. So much so I had a boss give me the title "Chip Master". I am the "SysOp" of this site.
Poor Man's IDS:
Since cyber criminals and big-tech companies combined are an ever increasing threat to all of our digital lives, which could spill over into our physical world, I'm taking steps to keep an eye on what my devices are chirping across the net and to whom. I'm recording my steps into this so maybe I can be of help to other security / privacy conscious users.
NOTE: I just pushed the initial version of my analysis software here. Its not fit for normal user consumption.
A couple of scenarios that came to light recently:
If you turn off the data services (cell,WiFi) on your android device for a week or so when you turn it back on the device becomes virtually comatose due to the flood of network traffic it produces. Give it some time, depending on how long its been off and it will start to become responsive again. What is getting passed around? Is it bad? We don't know.
We recently had an SSD die in a laptop of ours and we needed to temporarily replace it with a slow (aka power efficient) spinning disk. We found several of the well known news sites would bog down and literally lock the machine up for minutes, sometimes requiring me to SSH in and kill FireFox. The performance suck was entirely hard drive saturation. What was it doing reading our entire HDD? Sending it across the web? "Star Fleet Strength!" (Start Trek Movie #1).
killall firefoxI love that command.
Resources:
- Project files (source, sample block lists...)
- Project Wiki Notes about its purpose and use
C.H.I.P. Related Links:
- My C.H.I.P. Archives
- Chat @ Discord
- Archived wiki
NOTE: the original www.chip-community.org has fallen off-line.
SBCs that interest me since C.H.I.P. died:
- OrangePi Zero Teensy, very affordable and very useful.
- NanoPi Fire 2a LTS can almost compete with the C.H.I.P. in flexibility but at about 2.5x the price. Still less coin than a RaspberryPI.
- Beagle Bone Black may actually be able to take the place of CHIP in a PocketCHIP.
RaspberryPiThey have apparently partnered with M$. I have no use for such things and they are hostile to anyone speaking ill of M$. So its a mutual dislike.
My Current favorite MCU:
ATmega328P (aka Arduino chip). I like to use them either on the discontinued, but cloned everywhere, "Pro Mini" boards or just the bare 28pin dip.
My favorite is likely to change as I find more units to play with. But this little guy is seriously flexible and affordable!
More to follow...

